Discover hidden threats - past and present - with the only agentless SaaS platform built for independent threat hunting and cost-effective assessments.
What is a Threat Assessment?
As threats evolve to bypass prevention technologies and controls, organizations must periodically validate their IT environments are secure and controls are working properly. The challenge with this is that often an independent review is needed to get a clear, comprehensive picture of your security posture including vulnerabilities and possible cyber threats. Bringing in an external partner adds complexity, time, and often many teams don’t know where to begin when choosing a threat assessment vendor.
Another challenge is that traditional security assessments only evaluate vulnerabilities and risks of future compromise, they often do not look at past exposure, vulnerabilities, and risks.
Lastly, organizations must consider that some assessments require a permanently installed agent running 24/7 to detect threats on an endpoint.
Infocyte ASSESS
Infocyte leverages it’s platform to deliver a fast, minimally invasive and cost-effective Threat Assessment that goes deeper than any monitoring or antivirus tool to discover hidden threats.
Infocyte Threat Assessments determine if an attacker is currently active in your network, or has been in the recent past which helps eliminate the gap of only considering future risks to your current security posture.
- Infocyte has agent-based and agentless options for Threat Assessments. The agentless option simplifies deployment with no pre-install or permanent software agents minimizing impact to your network.
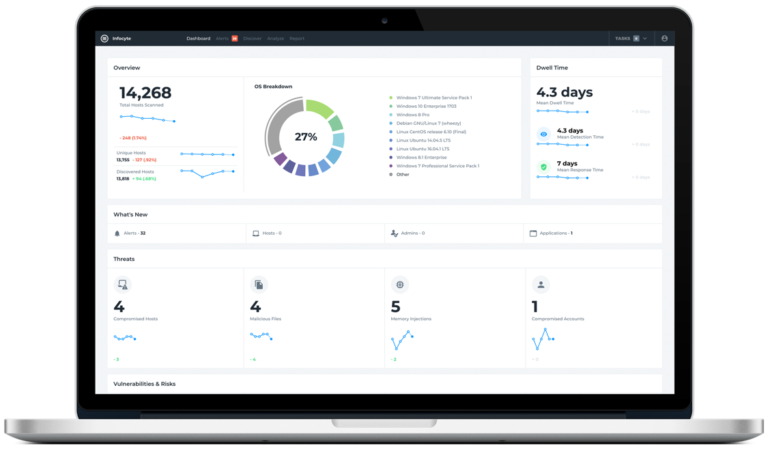
Platform Overview
Detect and Respond to Advanced Cyber Threats at Scale