SOLUTIONS
It's Time to get your cybersecurity
PBG is the AUTHORIZED SOLE DISTRIBUTOR of several Award Winning Systems Security Solutions. You can scroll down to know what our product have.
Accellion
Zero visibility. No control. High risk. Every day, employees put their organizations at risk of data breaches and compliance violations when they share IP, PII, PHI and other sensitive data with customers, suppliers and partners. But complex digital supply chains and complex IT infrastructure make it just too hard to protect these risky 3rd party communications. Not anymore! Introducing the industry’s first enterprise content firewall from Accellion.
The Accellion platform offers a secure data transfer channel that protects your sensitive information in transit and at rest. Designed with security in mind from the ground up: architecture, data protection, authentication and authorization, the Accellion platform offers enterprise-class flexibility and scalability that will accommodate your specific security requirements and infrastructure strategy.
Secure Deployment Options to Fit Your Needs
Deployment Options | Secure Data Transfer & Storage
- On-premise, private cloud, or hybrid cloud deployment
- Virtualized VMware and Hyper-V virtual environments
- Private or hybrid cloud deployment on AWS and Azure
- Hosted, compliant private cloud deployment by Accellion
- Keep data at the system of origin; no migration required!
Minimize Security Vulnerabilites and Reduc Maintenance Costs
Hardened Virtual Appliance | Secure Data Transfer & Storage
- Highly scalable and flexible deployment architecture
- Pre-configured for hardened, tight security
- Closed ports, disabled SSH, embedded anti-virus, encryption
- Fast, easy installation, patches and upgrades
- Ongoing security updates
Militarygrade Encryption In-transit and at Rest
Data Encryption | Secure Data Transfer & Storage
- AES 256 at rest, use and in transit
- Customer managed keys (bring your own key)
- FIPS 140-2 certification
- FedRAMP certified hosting
Bitdefender
Bitdefender is a Romanian cybersecurity and anti-virus software company. It was founded in 2001 by Florin Talpeş who is currently the CEO. Bitdefender develops and sells anti-virus software, internet security software, endpoint security software, and other cybersecurity products and services.
As of 2017, the software has about 500 million users worldwide. As of August 2017, Bitdefender ranks ninth in the global ranking of Windows anti-malware application vendors.
Bitdefender is a global security technology company that provides cutting edge end-to-end cyber security solutions and advanced threat protection to more than 500 million users in more than 150 countries. Since 2001, Bitdefender has consistently produced award-winning business and consumer security technology, and is a provider of choice in both hybrid infrastructure security and endpoint protection. Through R&D, alliances and partnerships, Bitdefender is trusted to be ahead and deliver robust security you can rely on.
Top international testing organizations and world-renowned software reviewers acknowledge Bitdefender’s solutions as the world’s most effective. In January 2015, Bitdefender won AV-Comparatives’ Product of the Year a second time, taking Gold awards in Proactive Malware Detection for its industry-leading heuristics, Real World Detection for accurate performance in real-life situations and Malware Removal for its thorough disinfection. At the same time, Bitdefender’s nearly undetectable impact on system performance won it Best Overall Speed.
For more information about Bitdefender products, visit the security press room. Bitdefender also publishes the HOTforSecurity blog, with stories from the underworld of internet fraud, scams and malicious software.
Prevents, detects and responds to all threats that might affect any of your organization’s assets. You get 360 degrees visibility, insights on the risks exposure and the tools to enhance the security posture. All of these, fully proven!

REAL-WORLD PROTECTION TEST MAR - APR 2018
The results of this test are based on a test set consisting of 620 test cases (such as malicious URLs), tested from the beginning of March till the end of April.

MALWARE PROTECTION TEST APR 2018
The Malware Protection Test assesses a security program's ability to protect a system against infection by malicious files before, during or after execution. For this test, 1470 recent malware samples were used.
Genians NAc
Genians provides the industry’s leading Network Access Control (NAC) solution, which ensures full visibility of all IP-enabled devices regardless of whether they are wired, wireless, or virtual. It also ensures that they conform to the highest levels of enterprise-mandated security and compliance.
Secure Any IP-Enabled Devices, No Matter What. Without securing devices, from a multitude of legacy devices to great wave of IoT devices at the edge, you will not be able to build the foundational cybersecurity framework required for securing your evolving networks.
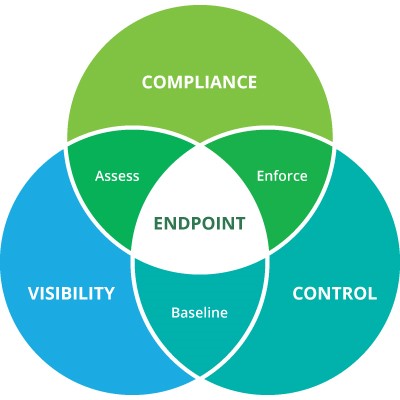
See every connected device holistically
- Identify all network-enabled devices and their attributes
- View from multiple perspectives (Device, IP, Switch Port, WLAN)
- Assess the compliance state of all connected devices
Control all connected devices contextually
- Enforce granular policies to regulate access
- Control endpoints’ systems configuration and network access
- Track endpoint activities and maintain IT security Ssecurity baseline
Automated all IT security tasks easily
- On-boarding process with workflows, approvals, and notifications
- Remove IT security silos by integrating with third-party solutions
- Automate the incident response and mitigation process.
iboss cloud security gateway
iboss Cybersecurity is a cutting-edge and market-leading Cybersecurity platform. iboss provides a secure gateway for thousands of businesses, corporations and educational institutions. The iboss platform protects against the ever-increasing number of threats to your network’s sensitive data.
iboss, a provider of network security solutions, today announced it achieved several company milestones in Q1, 2014. Sales grew 400 percent year-over-year, and the company made strategic new hires in marketing, finance, sales, operations and R&D. iboss expanded its San Diego team by 30 percent, and aims to double the current number of employees by year-end.
“San Diego is a hub for innovation, and it’s thrilling to be part of a community that is driving technology advancements in security,” said Paul Martini, CEO, iboss Cybersecurity. “As we continue to expand, we’re focusing on growing our team and tapping into the talented pool of local security executives. We’re also getting involved in local initiatives, such as the newly launched Cyber Center of Excellence, to make a continued impact on San Diego’s cyber security economy.”
New customers added in Q1 include Xerox, NutraSweet and Sears. iboss also secured contracts with Connecticut and Utah to aid in securing the states’ public networks. In addition to new contracts, iboss has achieved a 99.8 percent customer retention rate over the past three years.
iboss’ is expanding internationally as well. The company established new offices in Essex and the United Kingdom, and is adding to its sales and engineering staff in LatAm and APAC.
Helping large public- and private-industry organizations monitor and secure every aspect of their network in the age of BYOD and mobile devices, iboss’ growth has been largely organic. Key drivers include administrators seeking better security for mobile devices, solutions that scale better and manage bandwidth, methods to secure BYOD and better content visibility into what is occurring on networks. While legacy security vendors are ill-equipped to address these pain points, iboss’ solutions resonate with customers because they were developed specifically to address new and emerging security pain points. iboss is the only security vendor that offers solutions to proactively monitor outbound communications across all data channels and ports.
“We are determined to provide our customers with solutions that enable them to address complex network security challenges caused by cloud computing, the rush of new mobile devices entering the market and the increasing prevalence of sophisticated cyber threats. iboss’ increasing momentum is a testament to the fact that we’re meeting this goal,” continued Martini. “The success we’ve achieved also allows us to reinvest in our technology and growing our team. In 2014 we plan to significantly expand our international footprint, which will ensure we can improve network security for organizations across the globe.”
infocyte detection and response
The premier threat hunting solution for organizations possessing critical information and assets. Infocyte HUNT is an agentless software solution designed to detect hidden threats without the burden of complicated equipment or endpoint software installations.
Infocyte’s forensic automation and cloud-based threat intelligence arms security teams and assessors with the power to discover hidden malware and persistent threats, active or dormant, that have evaded existing defenses.
Infocyte is a developer of proactive cyber security solutions designed to identify threats and unauthorized activity on enterprise networks. Through their technology, Infocyte is pioneering the first objective breach discovery assessment that is both fast and affordable enough to perform regularly. Technology: The Pulse Intrusion Assessment Platform is an agent-less, on-premises appliance that scans network endpoints (ie. workstations and servers) for the presence of malware or unauthorized activity. The platform departs from traditional intrusion detection methods (ie. anti-virus) by combining patent-pending memory scanning techniques with signature-less forensic methods typically used in more expensive incident response services. The technology enables a 3rd party to scan a network to discover compromises, malware, and unauthorized activity six times faster than existing methods.
Seceon open threat management
Seceon Open Threat Management Platform enables organizations to see cyber threats quickly and clearly, and to stop them as they happen, preventing the infliction of extensive corporate damage. The platform was built to use elastic compute power to develop the industry’s first and only fully automated threat detection and remediation system. It detects all forms of threats as they happen, and automatically stops them in minutes. Anticipating attackers’ behavior choices, Seceon’s environment-agnostic solution identifies both known and unknown threats in real-time, preventing risk, damage or loss of valuable information.
Why PBG?
Powerbloc is the ONLY fully certify Technical Support distributor in the region covering Malaysia, Brunei, Philippines, Vietnam and Indonesia. We are also the authorized training facilitator for all of the above solutions.
- Technical Support and Maintenance
- Training
- Certified and Experienced Engineers
What You Get
Our Professional Services business are delivered by our team of skilled and qualified professionals that has vast number of years experience and expertise which they had gained from the deployment of many successful IT Projects.
- Assured Quality
- Proactive, Reliable and high Quality services
- Great Partnership








