Enterprise Content Firewall
Prevent Breaches and Compliance Violations from Risky Third Party Communications
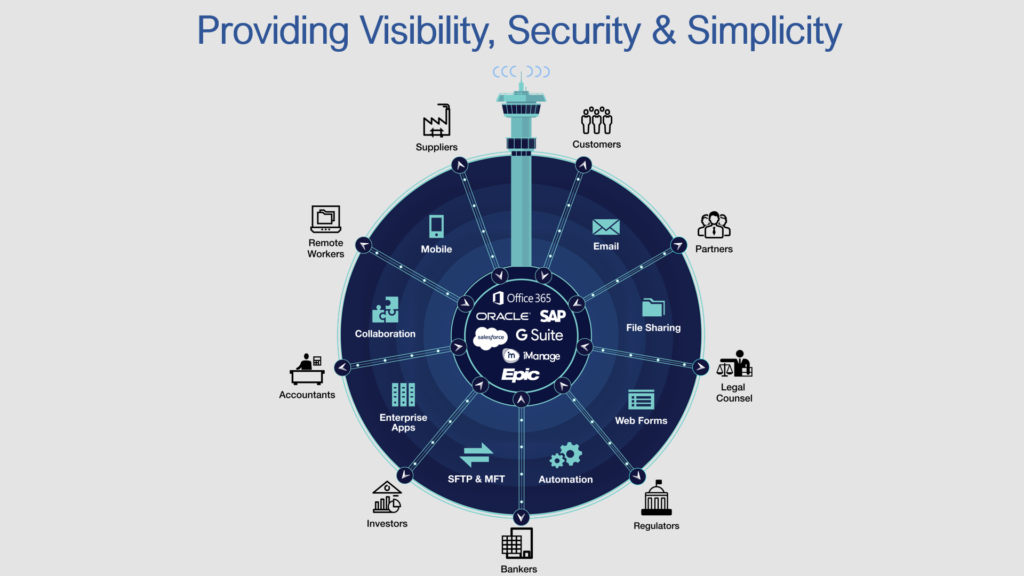
HOW IT WORKS
Consolidate
Comunications
Consolidate and Control 3rd Party Communications across email, file sharing , mobile, web forms, enterprise apps, managed file transfers, and SFTP by routing eacj channel through the enterprise content firewall. Protect your sensitive data more simplye, centrally and uniformly with every channel you add.
See Sensitive
Content
See Sensitive Content Shared with Customers, Suppliers, and Partners on the CISO Dasboard or your SIEM. Get a full picture of where content is going, who is accessing it, and how it is shared. The enterprise content firewall produces a single, normalized syslog that lays the foundation for threat detection and prevention.
Apply Uniform
Security
Apply Uniform Security and Governance Across Channels to prevent breaches and compliance violations. Define policies centrally for the content firewall to enforce as it inspects each transaction. Send every data exchange down a gauntlet of best-in-class security, including SSO, MFA, AV ATP, and DLP with a single point of integration.